07. AWS KMS Envelope Encryption 📨 🔑
While I worked at AWS during the publishing of this post / video, the views expressed here are my own and may not reflect those of my employer. Only publicly available material is used to put together the content of this article and video. The website and the Youtube videos are NOT monetized.
You can directly scroll down for the Youtube Video and Instructions used in the video are provided at the end of this article as well.
AWS KMS (key Management Service) provides the crypto as a service to its customers.
With KMS you can create symmetric and assymetric keys to perform cryptographic operations like
- Encrypt
- Decrypt
- Sign
- Verify
If you are new to KMS please refer this link to get to know the basic concepts around cryptography and KMS.
Whenver you encrypt or decrypt the data using KMS keys, the data is sent over to the KMS service.
Now this is not very efficient especially when large files (in GBs) are to be encrypted and decrypted. AWS KMS also puts a limit of 4Kb to be the maximum filesize on files directly encrypted using KMS.
So how do you efficiently encrypt and decrypt large or very large files using AWS KMS. Well, you use something called as envelope encryption.
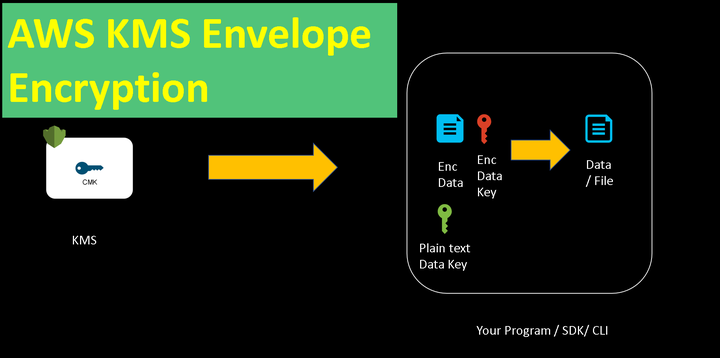
In Envelope encryption
- Instead of using the KMS keys directly for encryption, you generate a data key
- When you generate a data key using your KMS key, KMS sends you both plain text and the encrypted versions of the data key.
- You use the plain text data key to encrypt your data and delete the plain text key and the plain text data.
- Now you are left with encrypted data key and encrypted data.
Since you have encrypted the data locally this process is many times faster than sending the data over to KMS to encrypt (and decrypt)
When you have to decrypt the data.
- You decrypt the data key to plain text data key
- Derypt the data using the plaint text data key.
The process is called as envelope encryption or simply enveloping. This is the same process AWS uses to encrypt your data at rest in S3 as well as EBS etc.
In the Youtube video below, I explain what is Envelope Encryption with a Quick Demo
The commands/instructions used in the demo are provided below as well.
DEMO | AWS KMS | ENVELOPE ENCRYPTION
Please watch in full screen or on youtube directly
Linux / Mac / Windows (run with git bash) -
# Generate Data Key
aws kms generate-data-key --key-id <key id> --key-spec AES_256
# Decode the encrypted data key from base64 to binary
# In case of Linux and Mac use base64 -d instead of base64 -di
echo <encrypted_data_key> | base64 -di > enc_data_key.bin
#Encrypt the data with the plaintext data key
openssl enc -aes-256-cbc -pbkdf2 -in secret_file.txt -out encrypted_secret_file.txt -pass pass:<plaintext key>
#Simulating deletion of the plaintext data key
clear
# check for files
ls
#Decrypt the data key
aws kms decrypt --ciphertext-blob fileb://enc_data_key.bin
#Decrypt the data
openssl enc -d -aes-256-cbc -pbkdf2 -in encrypted_secret_file.txt -out decrypted_secret_file.txt -pass pass:<plaintext key>
Thank you for reading through
-Nikhil