19. Sovereignty Part 3/4 - Practical sovereignty - Sovereign solutions on Public Cloud

While I worked at Google during the publishing of this post / video, the views expressed here are my own and may not reflect those of my employer. Only publicly available material is used to put together the content of this article and video. The website and the Youtube videos are NOT monetized.
💡 This is part 3 of the (4 part) sovereignty series. Please checkout previous posts before you continue -
- What is sovereignty and why it can be the next big trend in cloud computing?
- Encryption to power data sovereignty on Google Cloud (Demo GCP EKM + KAJ and Confidential computing)
- ▶ Practical sovereignty - Sovereign solutions on Public Cloud
- Setting up sovereignty demo on GCP - Google cloud EKM + Confidential Computing + Ubiquitous Data Encryption/UDE + Thales CKM
Now that we have established - Sovereignty is important and have gone through a detailed data sovereignty video demo. Let’s revisit the different types of solutions offered by various cloud providers and find out which type is the most practical.
Sovereignty implementations can be classified as shown in the figure below.
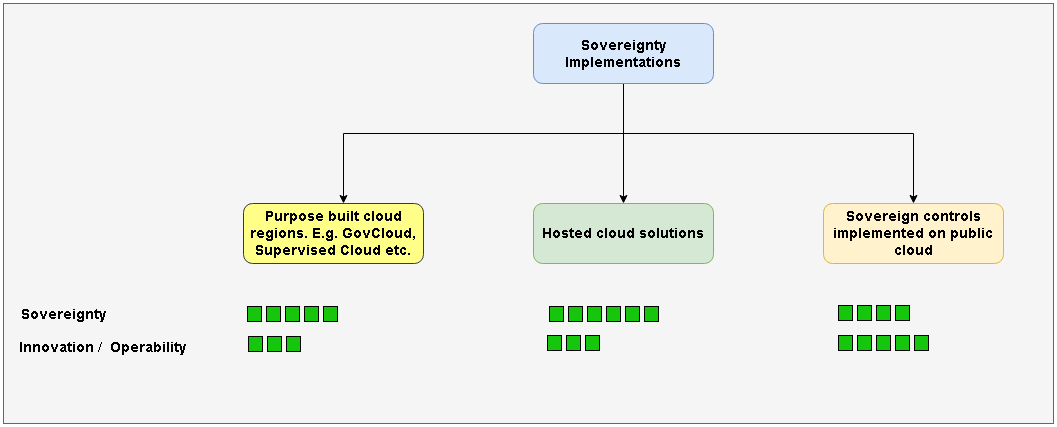
| Purpose built regions | Hosted Cloud Solutions | Sovereign controls on public cloud | |
|---|---|---|---|
| Definition | These are separate regions (viz. data centers) built and operated by the cloud provider which are only available to specific customers. These regions are not reachable from other public regions of the cloud. | Hosted cloud solutions run on a specialized/proprietary hardware in customers' on premises infrastructure. They generally only run a subset of cloud provider’s services in disconnected air gapped manner. The specialized/proprietary hardware is usually built and certified by the cloud provider | Sovereign controls like data residency, encryption, governance, sovereign support and transparency are implemented on the standard public cloud regions. |
| Available Products (click links for details) | Azure Government Cloud, AWS GovCloud , GCP supervised Cloud | Google Distributed Cloud, Azure Stack Hub, AWS Outposts | GCP - Cloud on Europe’s terms Initiative, T-Systems Sovereign Cloud powered by Google Cloud, Microsoft cloud for sovereignty |
| Relative costs | High | Very High | Low |
| Degree of sovereignty | High | Very High | Medium to high |
| Degree of Innovation and Operability | Medium | Low to Medium | High |
| Lag from the latest and the greatest SW & HW of cloud | Medium | High | Low to no lag |
| Practicality | Medium | Low | High |
| Additional expertise needed to operate a solution | Low | High | Low to Moderate |
| Relative Time to market for your solution | Slow | Slowest | Quickest |
❓ Now if you ask which implementation is the best? the answer is a resounding … depends 🤷♂️
It depends on the degree of sovereignty you / your customer needs and how much time you are willing to invest in getting the solution to the market using a given sovereignty implementation.
Sometimes it might not be your choice as an architect / project manager. Certain industries and governments might mandate you to build your solution on a particular sovereignty implementation.
❓ But if you ask which is the most practical implementation based on a requirement of reasonable sovereignty while maintaining pace of innovation and operational ease?
Well then box 3 from the figure above - sovereign controls implemented on public cloud is the right answer most of the times.
And that’s clear from the following announcements where the industry is demanding to build sovereignty in cloud for most regulated / soon to be regulated applications and data. And cloud providers are stepping up to build these solutions.
- Using public cloud to build sovereignty is the key - Microsoft - watch here
- Google Cloud - New data sovereignty controls for EU customers
- Thales Introduces S3NS in Partnership With Google Cloud and Unveils Its Offering
- AWS Digital Sovereignty Pledge: Control without compromise
💡 of course, sovereign & hosted clouds do and will continue to be a requirement for some use cases but the direction is to build and deliver sovereignty in public cloud.
Components of a public cloud sovereign solution
Building sovereignty on public cloud requires the cloud provider to implement following sovereignty controls
- Data residency guardrails
- Encryption
- Personnel access (data & resource) restrictions (e.g. EU persons from EU only can access etc.)
- Transparent, explicitely approved (before access) and verifiable (after access) customer data access, including cloud provider access
💡 You can read more about these controls in this Google cloud blog and Microsoft blog (search for sovereign controls) and AWS blog as well.
Before we understand how each of these controls are implemented by different cloud providers, let’s see how Google Cloud does it. Following is a video from official Google Cloud Tech Youtube Channel. The video includes a demo.
Now let’s continue our quest to delve deeper into how controls are implemented across top cloud providers.
Data residency
Cloud providers form some sort of boundary around regulated workloads. So in case of GCP it is manifested in Assured Workload folders and in case of Azure it is sovereign landing zone and Control Tower for AWS. Policies within these boundaries make sure that the data and resources stay within the compliant regions only.
Encryption
Data should be encrypted at rest and in use. Google cloud achieves this via Cloud EKM and Key Access Justifications. Microsoft cloud for sovereignty achieves this via Managed HSM and AWS has said it will achieve it via AWS KMS External Key Store (XKS)
I have demonstrated Google’s solution extensively in part 2 and how to set it up is explained in the part 4 of this blog series.
Personnel access
This is generally a requirement for data access by cloud provider employees who are supporting customer cases. Cloud providers achieve restrictions around personnel access (viz. who can access the data from where and when and for how long - e.g. EU resident can access data from EU only) by providing specilized support contracts and making sure that they have the compliant persons assigned to sovereign support cases.
An example of implementing personnel access control could be GCP - Assured Support
Transparency
Transparency is implemented in two ways.
- Information and resources given by cloud provider to customers to improve their trust in that cloud provider. e.g. Microsoft Government Security Program
- Logs of access by cloud provider (e.g. for performing support activities) made available to customers. e.g. GCP Access Transparency
- Explicit approval from customer for data access. e.g. GCP - Access Approval
Expertise
Now while this is not a control to be implemented, Customers may require some expertise to build using sovereign solutions implemented on public cloud. So many a times such an expertise is provided by a trusted partner.
Microsoft Cloud for Sovereignty is a partner-led and partner-first solution.
Moreover, involving a partner can also provide additional controls and sovereignty guarantees as demonstrated in following diagram from this Google cloud blog post.
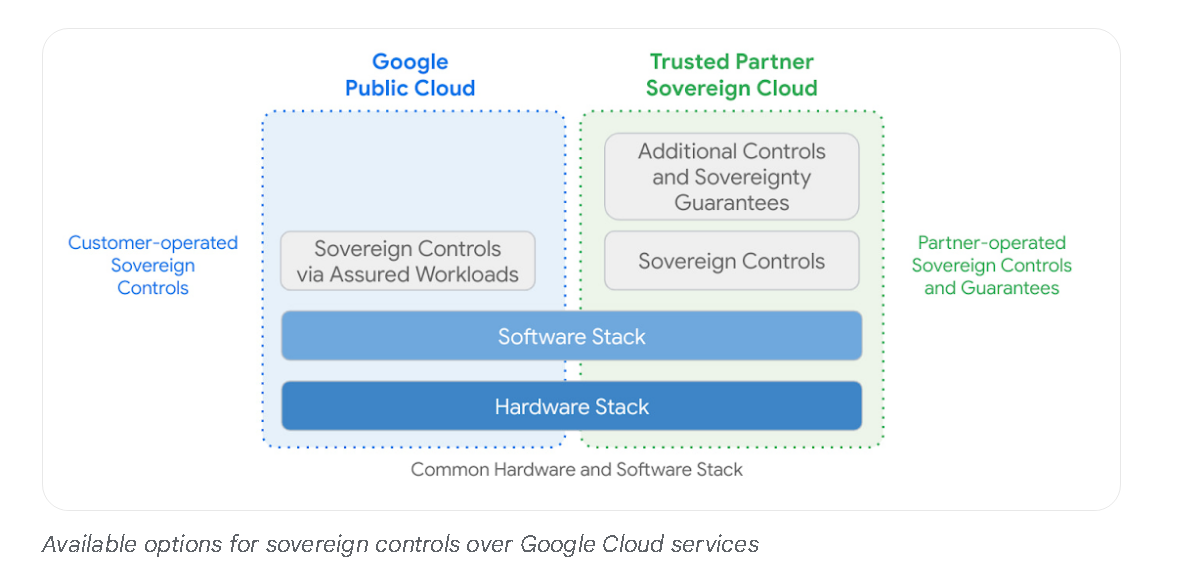
Example - T-Systems Sovereign Cloud Powered by Google Cloud
Another case for sovereign solution on public cloud - Productivity/ Collaboration Clouds
So we have established that the building sovereign solutions on public cloud is a compelling pattern for implementing sovereignty. However, when we are thinking about productivity cloud e.g. Office 356 and Google Workspace - Sovereignty has to be implemented in the cloud itself.
Can similar controls be implemented by the providers of these productivity solutions then?
The answer is yes.
And especially for Google workspace following articles - provide the details on implemented controls. We have also seen Client Side Encryption Demo from Google Workspace Official Youtube Channel in part 2
Conclusion
There are different implementation options when it comes to sovereignty on / by a cloud provider. We have compared all of them and have linked to concrete implementations. But with rapid movement of regulated workloads to cloud, most organizations might find building sovereignty on the public cloud most practical.
Thank you for reading through, Please like 👍, share 🔗 and comment ✍ if you found it useful.
-Nikhil